Introduction
TextQL provides enterprise-grade data analysis capabilities while maintaining the highest standards of security and governance, including compliance with SOC2 and HIPAA frameworks. Our platform enables organizations to leverage their data warehouse investments efficiently and securely, ensuring that sensitive data remains protected while delivering powerful analytical capabilities to users across the enterprise. This whitepaper outlines our comprehensive approach to security, access control, and data governance. From the ground up, TextQL has been designed with security and compliance in mind. Our platform incorporates industry best practices for data protection while providing flexible configuration options to meet diverse organizational needs. Whether deployed on-premises or as a hosted solution, TextQL ensures that your data remains secure and accessible only to authorized users under carefully controlled conditions.Security Architecture Overview
TextQL’s security architecture is built on multiple layers of protection, each working in concert to ensure comprehensive data security. Our platform employs a defense-in-depth approach, with security controls implemented at every layer of the stack. This begins at the network level with strict isolation and access controls, extends through authentication and authorization layers, and continues through to fine-grained data access policies at the query level. The security architecture is designed to be both robust and flexible, allowing organizations to implement their security policies while maintaining operational efficiency. This approach ensures that security measures enhance rather than impede legitimate data access and analysis activities.Authentication and Access Management
TextQL integrates seamlessly with existing enterprise authentication infrastructure through industry-standard OpenID Connect (OIDC) protocols. TextQL’s OIDC integration supports connection to common enterprise authentication solutions such as Microsoft Active Directory, Okta, Google Workspace, and more. This ensures that organizations can maintain consistent access control policies across their technology stack while leveraging existing identity management investments. Our platform supports role-based access control (RBAC) as a fundamental security principle. Roles can be mapped directly from your existing authentication provider, ensuring consistent access policies across your organization. These roles determine not only what data users can access but also what platform capabilities are available to them.Data Access Controls and Policies
TextQL enforces data access controls at multiple levels to ensure comprehensive security. At the database level, the platform respects and enforces native row-level security (RLS) policies, ensuring that users can only access data appropriate for their role and permissions.
Ontology-Based Governance
TextQL’s ontology system provides an additional layer of governance by modeling your data warehouse in a way that reflects your organization’s structure and security requirements.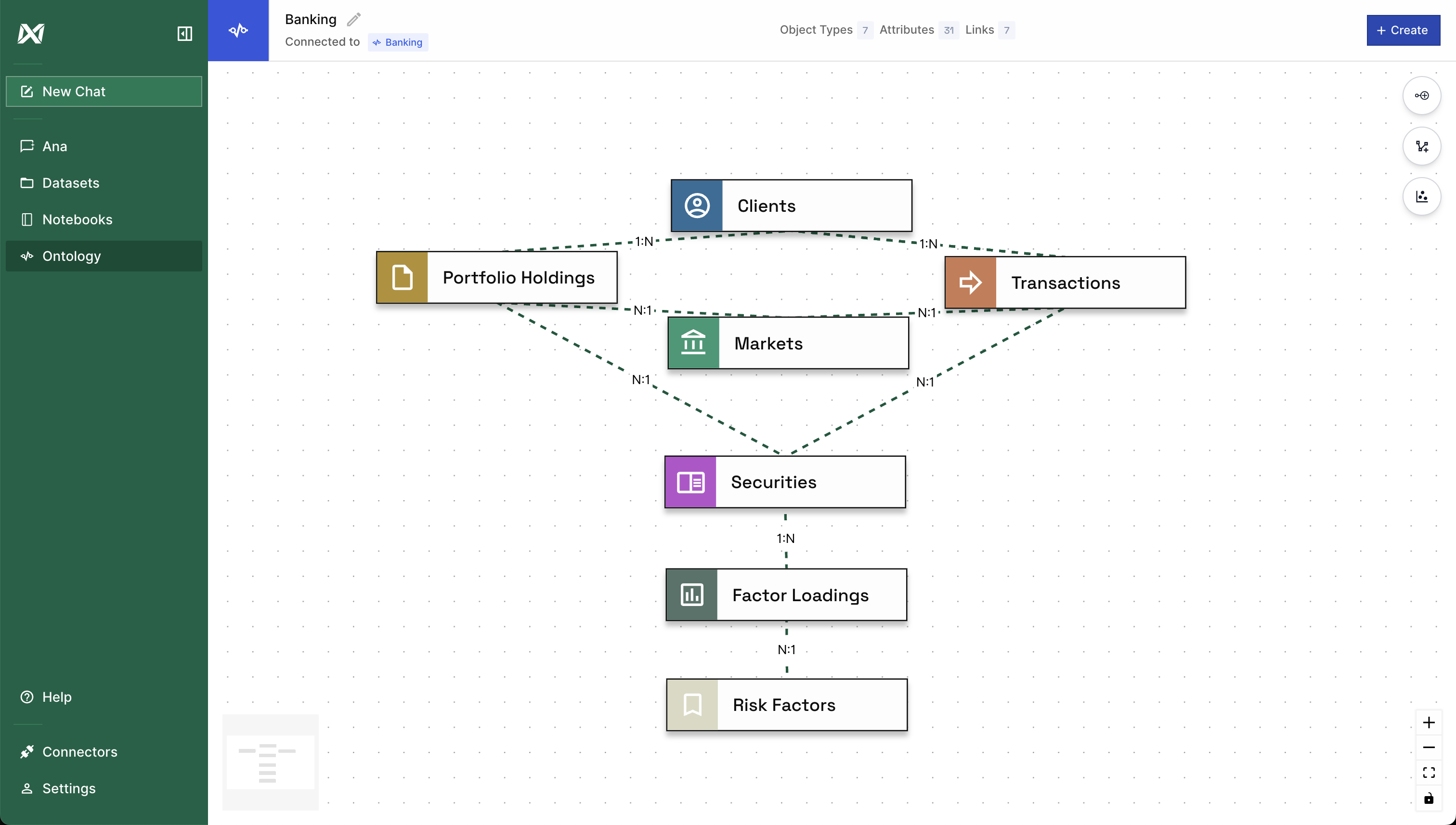
- Create different views of the data warehouse for different roles
- Configure access controls at a semantic level
- Ensure users only see and interact with data appropriate to their function
- Maintain consistent data governance across all interactions
Organizational Isolation
For organizations requiring the highest levels of data segregation, TextQL supports complete organizational isolation through our Organizations feature. This capability, available in on-premises deployments, enables the creation of entirely separated environments within the platform.
- Different business units
- Functional teams
- Geographic regions
- Regulatory requirements