Overview
TextQL supports Single Sign-On (SSO) via OpenID Connect (OIDC), allowing your users to authenticate using your organization’s identity provider instead of managing separate credentials.Supported Identity Providers
- Okta
- Microsoft Entra ID (Azure AD)
- Ping Identity
Getting Started
Before configuring SSO, you’ll need to access your TextQL organization as an administrator. If you don’t have an organization yet, you’ll need to create one first.Step 1: Login to TextQL
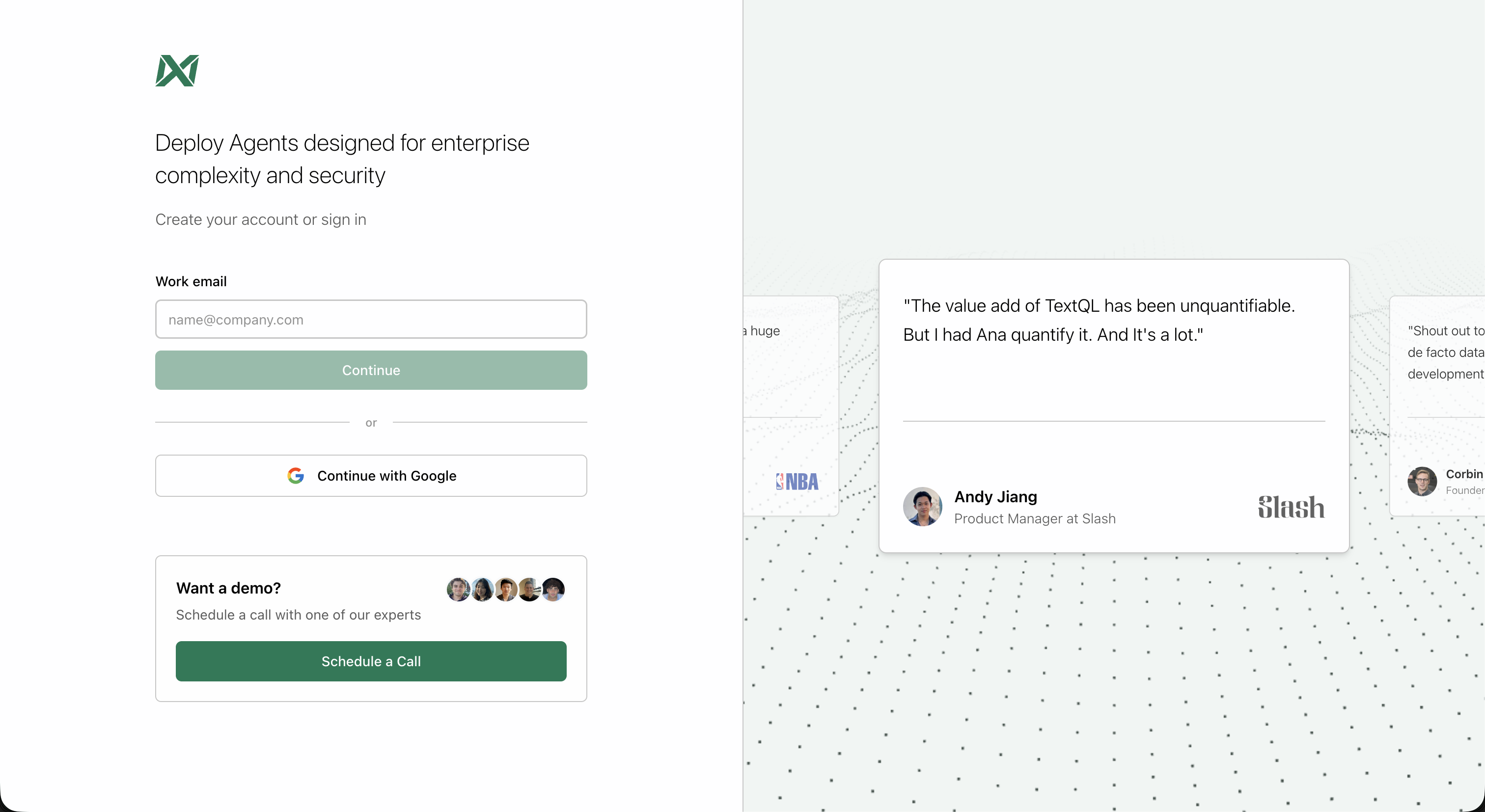
Navigate to the TextQL login page and sign in using one of the available methods:- Work email: Enter your email address to receive a magic link
- Continue with Google: Use your Google account for quick authentication
Step 2: Navigate to Settings
From the left sidebar, click on Settings to access your organization settings.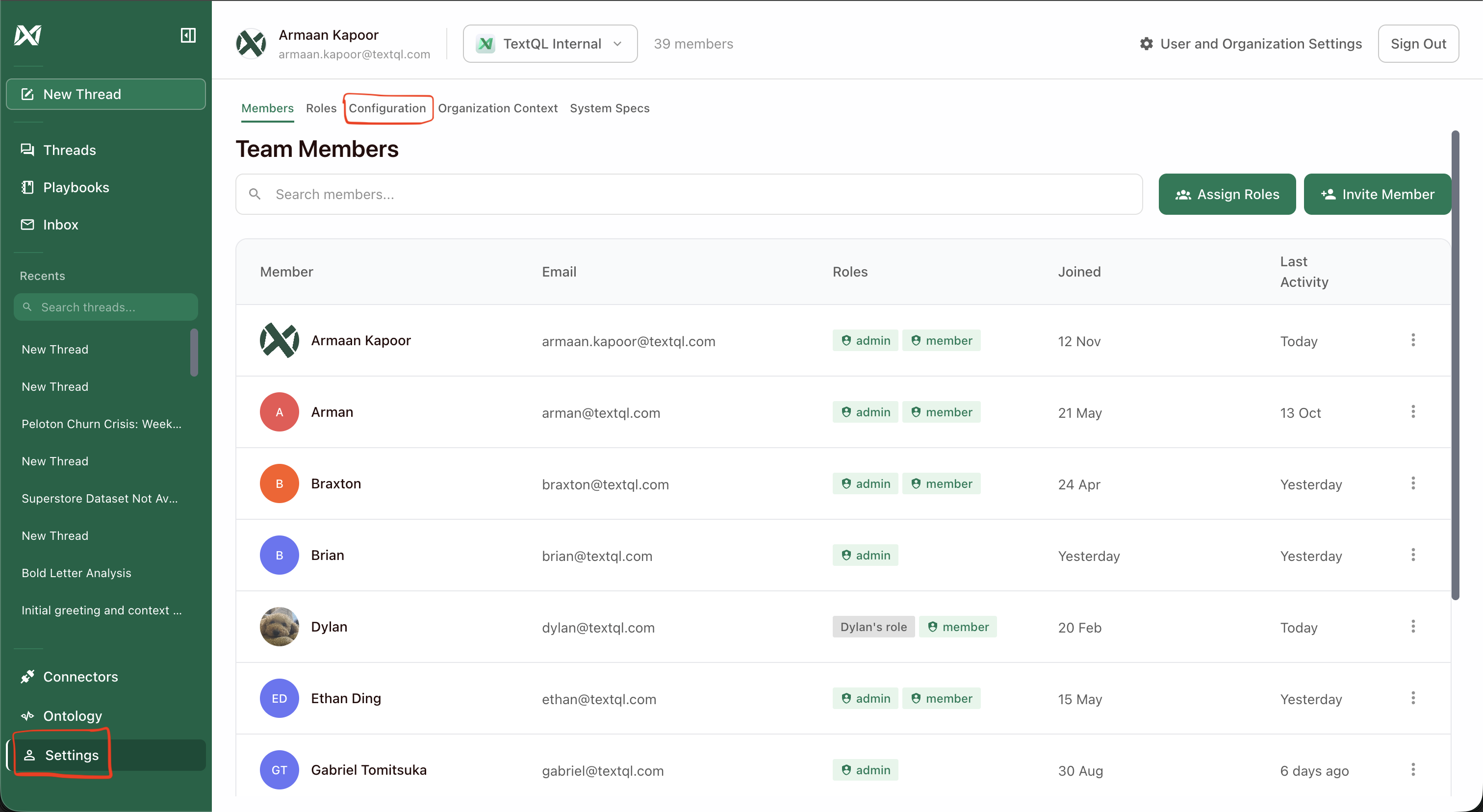
Step 3: Open OIDC Settings
In the Configuration tab, scroll down to the Authentication section and click OIDC Settings.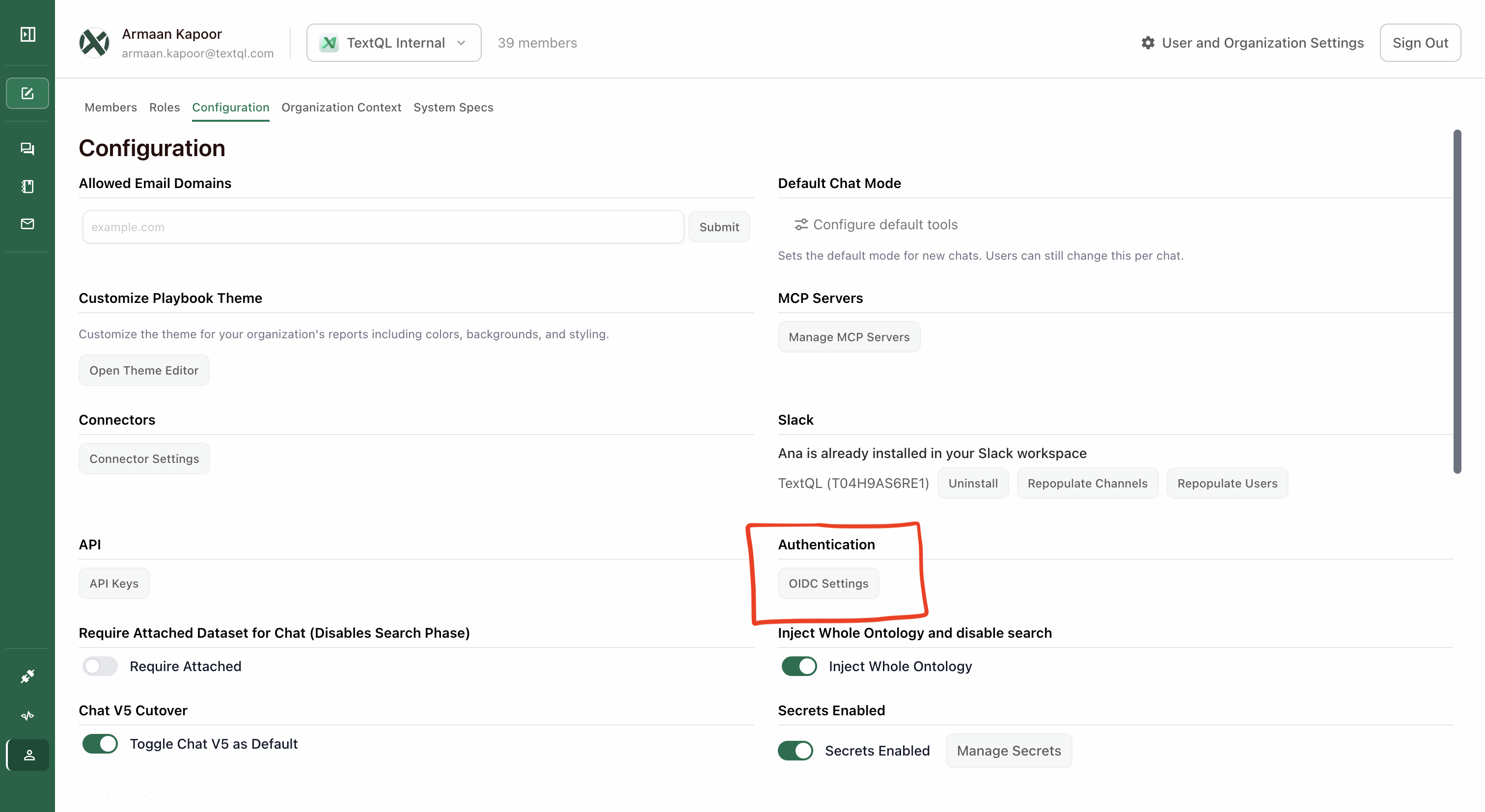
Step 4: Configure OIDC Fields
The OIDC Settings modal contains all the fields needed to connect your identity provider to TextQL.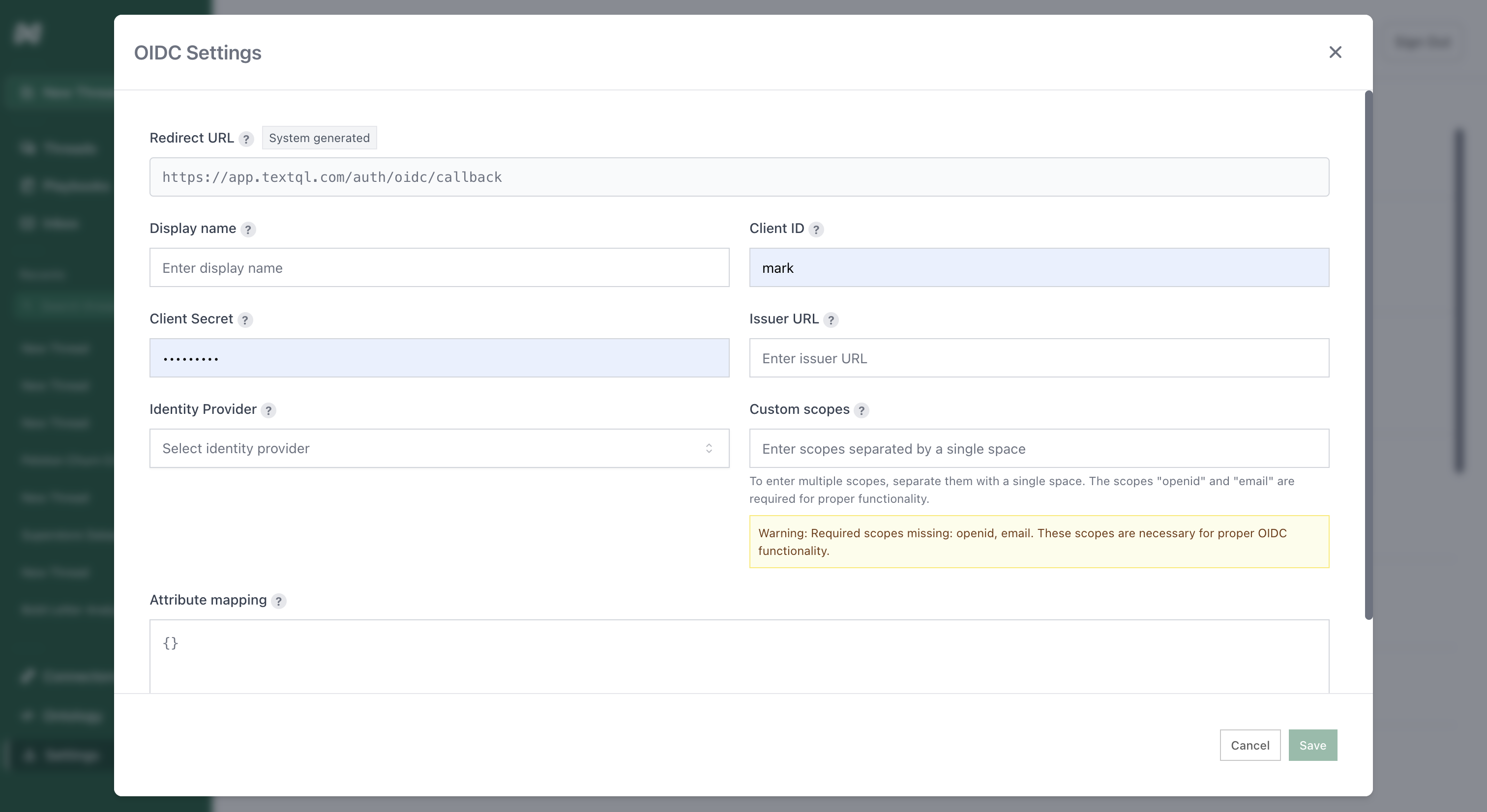
Redirect URL
This URL is system-generated and read-only. Copy this value and paste it into your identity provider’s configuration as the callback/redirect URI.Display Name
A friendly name for this SSO connection (e.g., “Company SSO”). This is what users will see during login.Client ID
The unique identifier for your application, provided by your identity provider when you create the OIDC application.Client Secret
The secret key used to authenticate your application. This is provided by your identity provider during OIDC app creation.Issuer URL
The base URL of your identity provider (e.g.,https://yourcompany.okta.com or https://login.microsoftonline.com/your-tenant-id).
Identity Provider
Select your identity provider from the dropdown:- Okta OIDC
- Microsoft OIDC
- Ping OIDC
Custom Scopes
OAuth scopes that determine what information your application can access. Required scopes areopenid and email.
Format: Space-separated values (e.g., openid email)
Attribute Mapping
JSON mapping of identity provider attributes to TextQL user fields. This allows you to map custom claims from your IdP to user properties. Example:How It Works
Once SSO is configured:- User visits the TextQL login page
- User enters their email address
- TextQL detects the email domain matches your configured OIDC organization
- User is automatically redirected to your identity provider
- User authenticates with their corporate credentials
- User is redirected back to TextQL and logged in
Testing
After saving your configuration:- Open a new incognito/private browser window
- Navigate to your TextQL login page
- Enter an email address from your organization’s domain
- Verify you’re redirected to your identity provider
- Complete authentication
- Verify you’re logged into TextQL
Troubleshooting
Users not being redirected to SSO
- Verify the email domain matches what’s configured in your OIDC settings
- Check that the OIDC configuration is saved and active
Authentication fails at identity provider
- Verify the Redirect URL is correctly configured in your IdP
- Check that the Client ID and Client Secret are correct
- Ensure users are assigned to the application in your IdP
Users redirected but not logged in
- Verify required scopes (
openidandemail) are configured - Check that the Issuer URL is correct
- Review attribute mapping to ensure email field is properly mapped
Security Considerations
- Client Secrets are stored encrypted in the database
- Only organization administrators can view or modify SSO settings
- Users must be assigned to the application in your identity provider to authenticate
- Sessions follow your organization’s token expiration policies